Recently I’ve been focusing on something I’ve overlooked for too long- monitoring. I wanted to share a quick guide on monitoring Debian / Ubuntu with SNMPv3 and PRTG as I couldn’t find any high level, up-to-date information readily available. I’ve gone as lightweight as possible and only installed snmpd to get disk space, CPU and memory monitoring working.
On the Debian / Ubuntu device you would like to monitor-
Update repositories
sudo apt-get update
Install snmpd
sudo apt-get install snmpd
Stop the snmpd service
sudo systemctl stop snmpd
Create credentials for SNMPv3 authentication
sudo nano /var/lib/snmp/snmpd.conf
Add the following line beneath the comment block at the top. Replace USERNAME, PASSWORD and ENCRYPTIONKEY with your values. Note the encryption key, which is simply a string shared with client and server
createUser USERNAME SHA PASSWORD AES ENCRYPTIONKEY
Edit the snmpd conf file
nano /etc/snmp/snmpd.conf
Comment out the following line-
agentAddress udp:127.0.0.1:161
Like so-
#agentAddress udp:127.0.0.1:161
Add the following line to allow remote access from our PRTG server-
agentAddress udp:161
And the following line to grant read only access to the user we created earlier-
rouser USERNAME priv
Save and close the file.
Start the snmpd service
sudo systemctl start snmpd
Over on the PRTG server, add a device
Add the IP address of the Linux device we were just working on
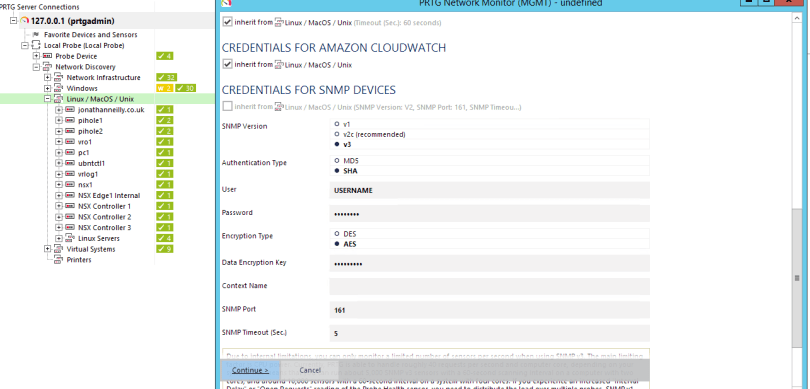
Add credentials, matching what was created on the Linux device previously
Select the device created, then Add Sensor
Narrow down sensors by selecting Linux/MacOS and SNMP then select the required sensor.
Give PRTG around a minute to collect data, then the sensor will be visible from the dashboard





Hi Jonathan,
Congratulations for your work !
I just stuck with couple of things you meant my instances private key is encryption key am i right?
How do mention it just like encryption name or content of key.
Think of the encryption key as being like a hash salt. Both the client and and server know the key value and use that to decipher encrypted messages. It should be a unique value. I tend to use a randomly generated password.
Hope this helps!